Directory Listing
How directory listing (indexing) can leak sensitive files and metadata, why it matters, and practical mitigations for web servers and cloud storage.
Description
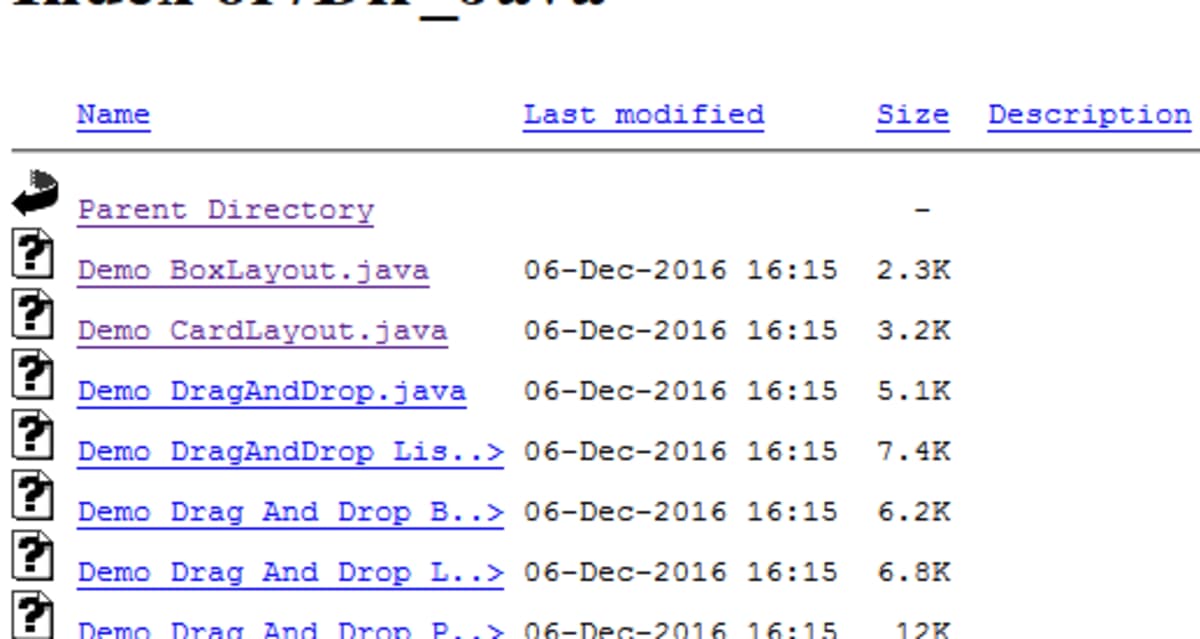
Directory listing (also called directory indexing) occurs when a web server or storage endpoint automatically generates a page listing the contents of a directory because no default index file (e.g., index.html) is present or indexing is explicitly enabled.
When unintentionally exposed, directory listings can reveal file names, sizes, timestamps, and direct download links. These files often include sensitive information such as configuration backups, archives, logs, credentials, or internal documentation all of which can significantly aid attackers during reconnaissance and exploitation.
Observation
Directory listings are frequently overlooked during hardening. They are commonly found in static sites, legacy applications, misconfigured S3/GCS buckets, and staging environments.
Impact
- Information disclosure: file names, metadata, and directory structure reveal sensitive resources.
- Reconnaissance: attackers can map application internals and locate high-value targets.
- Data leakage: exposed files (credentials, logs, exports) may enable direct compromise.
- Attack chaining: discovered artifacts can reveal endpoints, credentials, or code paths that enable further exploitation (e.g., SQLi, SSRF, RCE).
Even when files themselves are not directly sensitive, the contextual information gained can accelerate targeted attacks.
Common Examples
backup/,db_backups/,archives/with SQL dumps or ZIP files.git/directories leaking full source repositories.envorconfigs/with credentials and API keyslogs/with debug traces or internal identifiers- Upload folders containing scripts or executables
- Public cloud storage buckets (S3, GCS, Azure Blob) with object listing enabled
Detection
Quick checks include making direct HTTP requests to directory paths and observing the response. If the server returns an auto-generated HTML file listing, indexing is enabled.
Scanners, crawlers, and tools like dirb, ffuf, or Burp Suite will also flag directories that return 200 OK responses with file listings.
Remediation
Prioritized steps to mitigate Directory Listing:
- Disable directory indexing:
- Apache:
Options -Indexesin<Directory>or.htaccess. - Nginx:
autoindex off;in the relevantlocationorserverblock.
- Apache:
- Use default index files (
index.html,index.php) in all public directories. - Restrict access with authentication and least-privilege controls for sensitive directories and storage endpoints.
- Remove sensitive files from public web roots; store backups/configs outside of accessible paths.
- Harden cloud storage:
- Disable public object listing.
- Enforce least-privilege ACLs and bucket policies.
- Use pre-signed URLs for controlled access.
- Enforce file permissions so only the web server and admins can access sensitive files.
- Whitelist file types or deny dangerous extensions explicitly.
- Monitor & alert for unexpected directory responses (HTTP 200 on directories) or public object listings.
Example Configurations
- Apache
<Directory /var/www/html> Options -Indexes AllowOverride None </Directory> - Nginx
server { listen 80; server_name example.com; location / { root /usr/share/nginx/html; index index.html index.htm; autoindex off; } } - S3
- Enable Block Public Access.
- Deny
ListBucketto unauthenticated principals in bucket policies. - Use pre-signed URLs instead of public objects.
Verification
To confirm remediation:
- Request the directory URL and expect a redirect to an index file, a 403/404, or a login page.
- Automate periodic scans to catch regressions (e.g., after deployments or rebuilds).
References
Next Steps
If directory listings are found during testing:
- Review exposed artifacts for secrets and sensitive data.
- Consider related issues:
- Verbose Error Messages
- Metadata Service Exposure
Takeaway: Directory Listing is a low-effort, high-value fix. Disabling it reduces attacker reconnaissance opportunities and prevents easy information leaks. Make it a standard security control in deployment pipelines.
Last updated on
Information Disclosures
Overview of information disclosure vulnerabilities, their risks, and mitigations. This post serves as the entry point to categorized writeups on different forms of information leakage.
TLS / SSL information leakage
How TLS/SSL misconfiguration and implementation flaws can leak sensitive information and allow MitM, session hijack, or credential theft detection and remediation guidance.